Enable SSO for Your Organization
Looking for docs on how to add Single Sign-On support in your Supabase project? Head on over to Single Sign-On with SAML 2.0 for Projects.
Supabase offers single sign-on (SSO) as a login option to provide additional account security for your team. This allows company administrators to enforce the use of an identity provider when logging into Supabase. SSO improves the onboarding and offboarding experience of the company as the employee only needs a single set of credentials to access third-party applications or tools which can also be revoked by an administrator.
Supabase currently provides SAML SSO for Team and Enterprise Plan customers. If you are an existing Team or Enterprise Plan customer, continue with the setup below.
Supported providers
Supabase supports practically all identity providers that support the SAML 2.0 SSO protocol. We've prepared these guides for commonly used identity providers to help you get started. If you use a different provider, our support stands ready to support you.
Once configured, you can update your settings anytime via the SSO tab under Organization Settings.
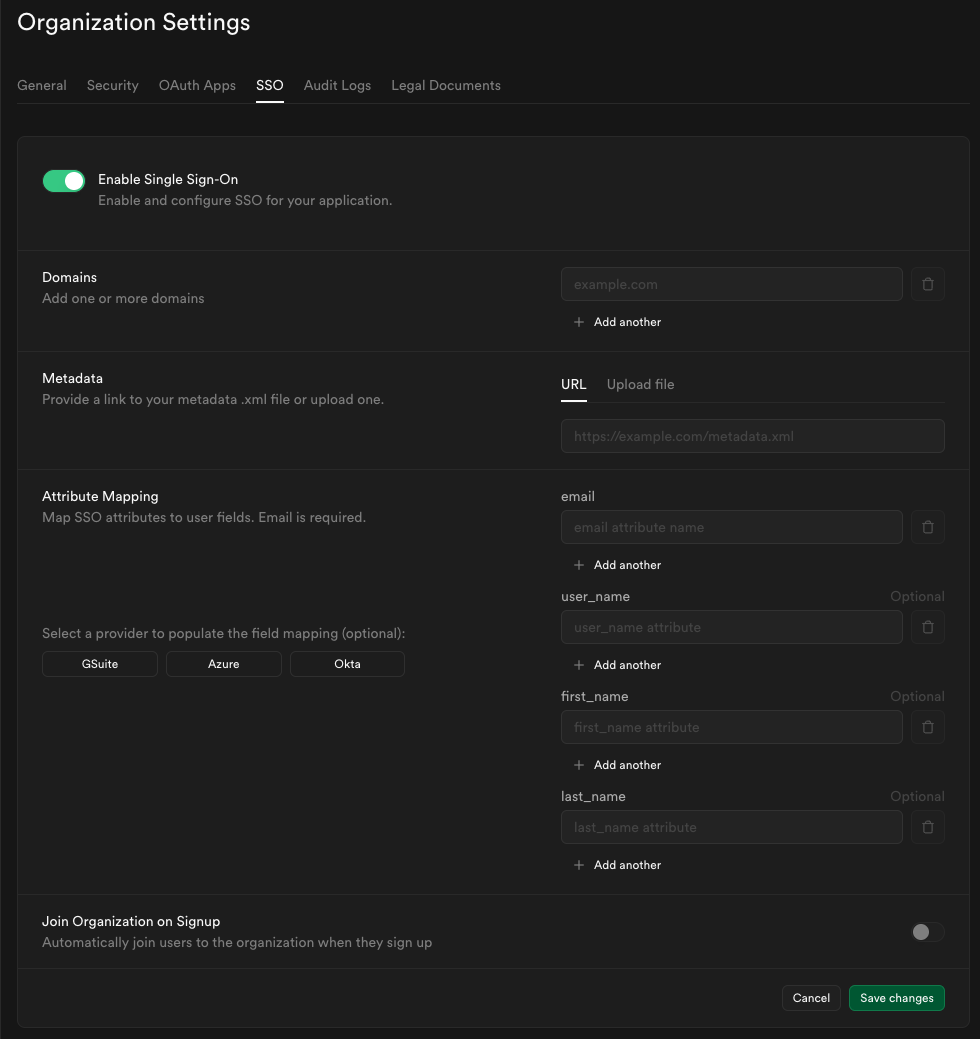
Key configuration options
- Multiple domains - You can associate one or more email domains with your SSO provider. Users with email addresses matching these domains are eligible to sign in via SSO.
- Auto-join - Optionally allow users with a matching domain to be added to your organization automatically when they first sign in, without an invitation.
- Default role for auto-joined users - Choose the role (e.g.,
Read-only,Developer,Administrator,Owner) that automatically joined users receive. Refer to access control for more information about roles.
How SSO works in Supabase
When SSO is enabled for an organization:
- Organization invites are restricted to company members belonging to the same identity provider.
- Every user has an organization created by default. They can create as many projects as they want.
- An SSO user will not be able to update or reset their password since the company administrator manages their access via the identity provider.
- If an SSO user with the following email of
alice@foocorp.comattempts to sign in with a GitHub account that uses the same email, a separate Supabase account is created and will not be linked to the SSO user's account. - SSO users will only see organizations/projects they've been invited to or auto-joined into. See access control for more details.
Disabling SSO for an organization
If you disable the SSO provider for an organization, all SSO users will immediately be unable to sign in. Before disabling SSO, ensure you have at least one non-SSO owner account to prevent being locked out.
Removing an individual SSO user's access
To revoke access for a specific SSO user without disabling the provider entirely you may:
- Remove or disable the user's account in your identity provider
- Downgrade or remove their permissions for any organizations in Supabase.